The People Who Made Privacy Possible
Cryptography is a declaration.
The people in these halls built systems that defied states. They wrote code when cryptography was treated as contraband. They stood for individual rights long before most understood that a battle was underway.
They are the quiet heroes we never deserved.
We remember them, and we thank them, for the freedoms their code made possible, and for the ones it allows us to defend.
"Cypherpunks write code. We know that someone has to write software to defend privacy, and we're going to write it." - Eric Hughes
Founders & Manifesto Era
The fathers of freedom understood they were in a world ruled by law but governed by control. They knew that without privacy, freedom was theater. So they built tools no one else understood, that would become the arsenal of the free.
-
 Timothy C. May
Timothy C. May
Visionary who authored the foundational The Crypto Anarchist Manifesto, Timothy C. May articulated the principles of crypto-anarchy, predicting how public-key cryptography and strong encryption would empower individuals to resist surveillance and censorship. As a co-founder of the Cypherpunks mailing list, he catalyzed the movement that inspired innovations like digital cash, anonymous networks, and privacy-enhancing technologies. His vision of a decentralized, cryptographically protected society, outlined in works like Libertaria in Cyberspace, profoundly influenced the development of cryptocurrencies and the global privacy movement
-
 Eric Hughes
Eric Hughes
Author of the seminal A Cypherpunk's Manifesto (1993), he articulated the foundational philosophy that privacy is a social duty and that "cypherpunks write code" to defend individual freedoms. As a co-founder and moderator of the original Cypherpunks mailing list, he fostered a global community that transformed cryptographic theory into practical tools for privacy, anonymity, and digital resistance. His advocacy and leadership catalyzed the development of technologies like PGP and inspired generations of privacy activists, making him a central architect of the cypherpunk ethos
-
 John Gilmore
John Gilmore
Visionary co-founder of the Electronic Frontier Foundation (EFF), he championed digital privacy and fought government surveillance through landmark activism and litigation. Instrumental in launching the Cypherpunks mailing list, he fostered a global community dedicated to advancing cryptography and resisting censorship. Gilmore was a key supporter of the GNU Project, free software, and open encryption, and his iconic phrase, "The Net interprets censorship as damage and routes around it", encapsulates the cypherpunk ethos of resilience and decentralization. His advocacy for strong cryptography and opposition to export controls helped shape the legal and technical landscape for privacy tools
-
Perry Metzger
Co-founder of the Cypherpunks mailing list, he catalyzed the global exchange of ideas on privacy, digital cash, and anonymous communication, directly influencing the development of remailers and practical cryptographic tools. An early advocate for strong encryption, he bridged theoretical cryptography and real-world implementation, providing technical infrastructure and thought leadership that helped shape the cypherpunk movement's pragmatic approach to digital freedom, censorship resistance, and privacy-by-design
-
 Jude Milhon (St. Jude)
Jude Milhon (St. Jude)
Visionary hacker and writer who coined the term "cypherpunk," catalyzing a movement dedicated to privacy, cryptography, and digital autonomy. As an early member of the Community Memory Project, she championed accessible, decentralized technology and advocated for the empowerment of marginalized voices in computing. Through works like Hacking the Wetware: The NerdGirl's Pillow Book, she promoted an inclusive, feminist hacker culture and inspired generations to see technology as a tool for liberation and resistance against surveillance
-
 John Perry Barlow
John Perry Barlow
Co-founder of the Electronic Frontier Foundation (EFF), he authored the influential A Declaration of the Independence of Cyberspace, which boldly asserted the Internet as a domain of freedom, immune to traditional government control. His manifesto inspired generations of cypherpunks and digital rights activists, articulating a philosophy of online liberty, privacy, and resistance to censorship that shaped the ethos of the digital rights movement and continues to influence debates on surveillance and decentralization
-
 Phil Zimmermann
Phil Zimmermann
Introduced mass-accessible strong encryption by creating PGP (Pretty Good Privacy) in 1991, making public-key cryptography available to activists, journalists, and ordinary citizens worldwide. His release of PGP sparked the first Crypto Wars, challenging US export controls on cryptography and catalyzing global debate over privacy rights versus government surveillance. Zimmermann's work embodied the cypherpunk ethos, empowering individuals to protect their communications and inspiring later privacy tools and movements. His advocacy and technical achievements cemented the principle that privacy is a fundamental right in the digital age
-
 Brewster Kahle
Brewster Kahle
Digital archivist who founded the Internet Archive, a nonprofit library that preserves billions of web pages, books, and digital artifacts, ensuring public access to information beyond the reach of censorship or deletion. Championed the ideal of "universal access to all knowledge," advancing cypherpunk values by defending the right to read, privacy in digital libraries, and resistance to digital erasure. His advocacy for open access and long-term digital preservation has made the Archive a critical resource for journalists, activists, and researchers confronting surveillance and information control
-
 Wau Holland
Wau Holland
Co-founder of the Chaos Computer Club (CCC), he advanced the articulation of hacker ethics and fought for digital civil rights, privacy, and transparency in the information age. Advocated for the responsible use of technology, public understanding of cryptography, and the necessity of secure communications as a bulwark against state and corporate surveillance. His activism and public demonstrations, such as the 1984 BTX hack, inspired generations of cypherpunks and laid the groundwork for Europe's digital rights movement, influencing debates on anonymity, decentralization, and the moral imperative of ethical hacking
-
 Andy Müller-Maguhn
Andy Müller-Maguhn
Key architect of hacker ethics and digital rights, he shaped global debates on privacy and encryption as a leading voice of the Chaos Computer Club, Europe's most influential hacker collective. As a former ICANN board member, he championed decentralized, open Internet governance and defended user privacy against surveillance. His advocacy for strong encryption, transparency, and ethical hacking has inspired generations to resist censorship and protect civil liberties in the digital age, advancing core cypherpunk ideals of autonomy and secure communication
Cryptography Architects
They took math too pure to weaponize and did it anyway, proving that ideas can defend people and laying the foundations for all cypherpunks.
-
 Claude Shannon
Claude Shannon
Established the scientific foundation of modern cryptography by applying information theory to encryption in his seminal 1949 paper, Communication Theory of Secrecy Systems. Introduced the concepts of entropy, confusion, and diffusion, which underpin the design of all secure ciphers. His work transformed cryptography from secretive art to rigorous science, enabling the development of privacy tools and protocols essential to cypherpunk ideals of secure, private digital communication
-
 Alan Turing
Alan Turing
Mathematician whose theoretical work on Turing machines and computability established the mathematical basis for modern cryptography, laying the groundwork for secure digital communication and privacy. At Bletchley Park, he led efforts to break the Enigma machine, demonstrating the power of computation in cryptanalysis and inspiring later developments in privacy technology, secure protocols, and the pursuit of digital freedom that underpin cypherpunk ideals
-
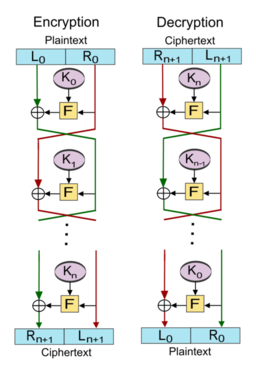
 Horst Feistel
Horst Feistel
Introduced modern symmetric cryptography by inventing the Feistel network, a foundational structure for block ciphers that enables secure, efficient encryption. His work on Lucifer directly led to the creation of the Data Encryption Standard (DES), which became the first widely adopted federal encryption standard and influenced countless later algorithms, including AES. By formalizing the round-based model of encryption, he provided the technical backbone for privacy-preserving technologies that underpin secure digital communications, anonymous transactions, and the cypherpunk movement's vision of individual privacy in the digital age
-
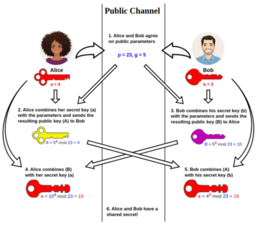
 Whitfield Diffie
Whitfield Diffie
Pioneer who co-invented public-key cryptography and revolutionized secure digital communication through the groundbreaking 1976 paper New Directions in Cryptography, introducing the Diffie-Hellman key exchange that enabled strangers to establish shared secrets over insecure channels without prior arrangement. Served as Chief Security Officer at Sun Microsystems and Vice President for Information Security at ICANN, advancing privacy-by-design principles in internet infrastructure. Together with Martin Hellman and Ralph Merkle, received the 2015 Turing Award for fundamental contributions to modern cryptography, establishing the technical foundation for secure email, e-commerce, and privacy tools like PGP and Bitcoin, embodying cypherpunk ideals of individual autonomy and resistance to surveillance
-
 Martin Hellman
Martin Hellman
Cryptographer who co-invented public-key cryptography, fundamentally transforming digital security through the 1976 landmark paper New Directions in Cryptography that introduced the Diffie-Hellman key exchange, enabling secure communications without pre-shared secrets. As Professor Emeritus at Stanford University, championed the right of cryptographic researchers to publish openly during the first Crypto Wars, successfully defending academic freedom against government restrictions. Awarded the 2015 Turing Award alongside Whitfield Diffie, his work laid the groundwork for modern internet security, encrypted messaging, digital signatures, and cryptocurrencies, directly empowering cypherpunk principles of decentralization, privacy, and individual digital rights in an era of pervasive surveillance
-
 Ralph Merkle
Ralph Merkle
Inventor of the foundational Merkle tree, he overhauled secure data verification and integrity, enabling scalable authentication for digital signatures, cryptocurrencies, and decentralized systems. As an early pioneer of public-key cryptography, his 1974 work on public-key distribution laid the groundwork for secure, private online communication. Merkle's innovations underpin privacy-preserving technologies such as blockchain, anonymous digital cash, and secure messaging, directly advancing cypherpunk ideals of decentralization, anonymity, and individual empowerment
-
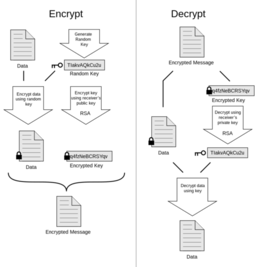
 Ron Rivest
Ron Rivest
Co-inventor of the RSA algorithm, the first practical public-key cryptosystem enabling secure digital communication and authentication, revolutionizing internet security and e-commerce. Institute Professor at MIT and founder of its Cryptography and Information Security Group, he designed influential symmetric ciphers (RC2, RC4, RC5) and cryptographic hash functions (MD4, MD5), shaping modern encryption standards. Co-founded RSA Data Security and VeriSign, advancing commercial cryptographic infrastructure, and co-authored the seminal textbook Introduction to Algorithms. Recipient of the 2002 Turing Award, his work embodies cypherpunk ideals by making strong encryption accessible globally, defending privacy, and enabling secure, decentralized digital communications that resist surveillance and censorship
-
 Adi Shamir
Adi Shamir
Israeli cryptographer who co-invented the RSA algorithm, establishing the foundation for modern internet security and digital signatures through practical public-key cryptography. Professor at the Weizmann Institute, he pioneered Shamir's Secret Sharing scheme for secure key distribution, co-developed visual cryptography, and co-discovered differential cryptanalysis with Eli Biham, exposing vulnerabilities in encryption systems and strengthening global cryptographic practices. Co-founded RSA Data Security to commercialize secure communications, and received the 2002 Turing Award for contributions to cryptography. His innovations in secure multi-party computation, zero-knowledge proofs, and attack methodologies have advanced cypherpunk principles by empowering individuals with tools for anonymous communication, privacy protection, and resistance to surveillance in the digital age
-
 Leonard Adleman
Leonard Adleman
Co-inventor of the RSA algorithm who reshaped digital security by enabling practical public-key cryptography and digital signatures, making secure internet communications and e-commerce possible at global scale. Distinguished Professor at the University of Southern California, he co-developed the Adleman-Pomerance-Rumely primality test, advancing algorithmic number theory essential to cryptographic security. Founded the field of DNA computing, demonstrating biological computation's potential for solving complex problems, and coined the term "computer virus," shaping cybersecurity discourse. Recipient of the 2002 Turing Award and co-founder of RSA Data Security, his work embodies cypherpunk values by democratizing strong encryption, enabling anonymous secure communications, and defending individual privacy against centralized surveillance and control
-
 David Chaum
David Chaum
Invented anonymous digital transactions with digital cash and mix networks, laying the cryptographic foundation for modern privacy-preserving currencies. His seminal 1983 paper, Blind Signatures for Untraceable Payments, introduced blind signatures, enabling untraceable payments and inspiring protocols behind Bitcoin, Zcash, and anonymous communication systems. His work directly shaped the cypherpunk vision of privacy, decentralization, and digital freedom
-
 Taher Elgamal
Taher Elgamal
One of the fathers of modern digital privacy who invented the ElGamal encryption system, a foundational public-key cryptosystem still used in protocols like PGP and cryptocurrencies. As chief architect of SSL/TLS, he enabled secure, encrypted web communications, making online privacy and e-commerce possible. His innovations bridged academic cryptography and real-world infrastructure, directly empowering cypherpunk ideals of secure, decentralized communication and individual privacy online
-
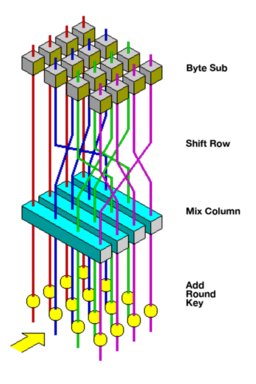
 Joan Daemen
Joan Daemen
Belgian cryptographer who co-designed Rijndael, the cipher selected as the Advanced Encryption Standard (AES) in 2001, becoming the world's most widely deployed encryption algorithm protecting everything from HTTPS to cryptocurrencies. Professor at Radboud University, he co-designed the Keccak cryptographic hash selected as SHA-3 by NIST in 2012, further advancing secure hashing standards. Received the 2017 Levchin Prize for Real World Cryptography and an ERC Advanced Grant for research on symmetric cryptography foundations. His open, transparent design philosophy, emphasizing mathematical elegance, rigorous peer review, and resistance to backdoors, embodies cypherpunk principles by making robust, auditable encryption accessible to billions worldwide, defending privacy and autonomy against mass surveillance
-
 Vincent Rijmen
Vincent Rijmen
Belgian cryptographer who co-designed Rijndael, the block cipher selected as the Advanced Encryption Standard (AES) by NIST in 2000, revolutionizing global data security and enabling secure communications at planetary scale. Professor at KU Leuven's COSIC lab and adjunct professor at the Selmer Center, he was named Fellow of the International Association for Cryptologic Research in 2019 for co-designing AES and advancing symmetric cryptanalysis. His research on side-channel attacks, block cipher design, and cryptographic theory has shaped modern security protocols, directly supporting cypherpunk ideals by ensuring that strong, open source encryption remains accessible to all, protecting individual privacy and enabling decentralized, censorship-resistant systems
-
 Daniel J. Bernstein (djb)
Daniel J. Bernstein (djb)
Cryptographer who transformed the world's privacy and security with the creation of Curve25519, a widely used elliptic curve for fast, secure public-key cryptography, and ChaCha20, a stream cipher now standard in TLS and VPNs. Developed qmail, a secure mail transfer agent, and dnscrypt, enhancing DNS privacy. His landmark lawsuit, Bernstein v. United States, established that publishing cryptographic code is protected free speech, setting a precedent for digital rights and cypherpunk activism. His work underpins secure messaging, cryptocurrencies, and privacy tools, embodying the cypherpunk ethos of empowering individuals through strong cryptography and open research
-
 Bruce Schneier
Bruce Schneier
Advanced modern cryptography by designing the Blowfish and Twofish ciphers, and demystified cryptographic protocols for the public through his influential book Applied Cryptography, which became a foundational text for the cypherpunk movement. Coined the term "security theater" to critique superficial security measures, and consistently advocated for strong encryption, privacy rights, and transparent security policy. His prolific writing, including Liars and Outliers and A Hacker's Mind, shaped public understanding of trust, surveillance, and digital freedom, inspiring generations of privacy advocates and technologists
-
 Tanja Lange
Tanja Lange
Pioneering cryptographer whose research in elliptic-curve cryptography and post-quantum cryptography has shaped the future of secure communications. Co-creator of SafeCurves, she has advanced the analysis and selection of cryptographic curves resistant to known attacks, directly influencing standards for privacy-preserving protocols. Her leadership in developing quantum-resistant algorithms, including contributions to NIST post-quantum cryptography standardization, has been crucial for safeguarding digital privacy against emerging threats, embodying the cypherpunk ethos of proactive security and transparency
-
 Neal Koblitz
Neal Koblitz
Co-inventor of elliptic-curve cryptography (ECC), he redefined public-key cryptography by introducing mathematical techniques that enable strong encryption with smaller keys, boosting both efficiency and security for privacy-focused protocols. His work underpins secure messaging, cryptocurrency wallets, and privacy-preserving systems, including Bitcoin and Signal, embodying cypherpunk ideals of decentralized, robust digital privacy. Koblitz's advocacy for cryptographic rigor and his foundational research in number theory have profoundly shaped the landscape of modern secure communications and digital rights
-
 Victor S. Miller
Victor S. Miller
Introduced elliptic-curve cryptography (ECC), co-inventing it independently with Neal Koblitz, and revolutionized public-key cryptography by enabling strong encryption with smaller key sizes. This breakthrough made secure communications feasible for mobile devices, smart cards, and embedded systems, directly impacting privacy technologies and protocols used in secure messaging, cryptocurrency wallets, and TLS/SSL. His work underpins modern privacy infrastructure, advancing cypherpunk ideals of accessible, robust encryption for all
-
 Shafi Goldwasser
Shafi Goldwasser
Pioneer who co-invented zero-knowledge proofs, enabling parties to prove knowledge of information without revealing the information itself, fundamentally advancing privacy-preserving cryptographic protocols. As RSA Professor at MIT and Professor at the Weizmann Institute, co-developed probabilistic encryption, establishing the gold standard for semantic security in modern cryptography. Awarded the 2012 Turing Award with Silvio Micali for revolutionizing cryptographic science, and two Gödel Prizes for groundbreaking work on interactive proof systems. Co-founder and Chief Scientist of Duality Technologies, advancing secure multi-party computation and homomorphic encryption, her innovations power anonymous authentication, privacy-preserving blockchain systems like Zcash, and secure digital voting, embodying cypherpunk principles of cryptographic resistance to surveillance and centralized control
-
 Silvio Micali
Silvio Micali
Cryptographer who co-invented zero-knowledge proofs, transforming privacy and authentication by allowing verification of statements without revealing underlying secrets, foundational to modern secure protocols. Ford Professor at MIT, he co-developed probabilistic encryption with Shafi Goldwasser, establishing provable security frameworks that underpin internet cryptography. Awarded the 2012 Turing Award for revolutionizing cryptography, and recipient of the Gödel Prize for interactive proof systems and verifiable random functions. Founded Algorand, a pure proof-of-stake blockchain advancing scalable, decentralized consensus. His work on verifiable random functions, secure multi-party computation, and Byzantine agreement has empowered cypherpunk ideals by enabling anonymous authentication, privacy-preserving cryptocurrencies, and trustless distributed systems resistant to censorship and manipulation
-
 Cynthia Dwork
Cynthia Dwork
Pioneer who co-invented the concept of proof-of-work in 1992 to combat email spam, laying the cryptographic foundation for decentralized consensus mechanisms that would later enable Bitcoin and blockchain technology. Distinguished Scientist at Microsoft Research and Gordon McKay Professor at Harvard University, she co-invented differential privacy, a rigorous mathematical framework enabling statistical analysis while protecting individual privacy, now standard in systems from Apple to the U.S. Census. Recipient of the Gödel Prize, Dijkstra Prize, and Knuth Prize, her work on fairness in algorithmic decision-making and privacy-preserving computation has profoundly advanced cypherpunk principles by providing mathematical tools to resist surveillance, protect anonymity, and ensure that decentralized systems remain trustless and secure
-
 Moni Naor
Moni Naor
Cryptographer who co-invented the proof-of-work concept in 1992, introducing computational puzzles as a defense against spam and denial of service attacks, a breakthrough that would later inspire the consensus mechanism underlying Bitcoin and blockchain technology. Professor at the Weizmann Institute of Science, his pioneering research spans visual cryptography, memory-hard functions, and non-malleable cryptography, advancing secure authentication and tamper-resistant protocols. Recipient of the Gödel Prize and Paris Kanellakis Award, his work on hardness-based security and privacy-preserving data structures has shaped modern cryptographic systems, enabling decentralized, censorship-resistant networks and embodying cypherpunk ideals of individual privacy, trustless consensus, and resistance to centralized control
-
 Ross Anderson
Ross Anderson
Pioneered the field of security engineering by exposing systemic failures in cryptographic systems and advocating for a holistic approach that integrates technical, human, political, and economic factors. Authored the influential textbook Security Engineering, which has shaped the understanding of privacy, anonymity, and secure system design for generations of cryptographers and cypherpunks. His research on real-world vulnerabilities, including banking security and medical device privacy, has driven reforms and inspired the cypherpunk ethos of skepticism toward centralized trust and the relentless pursuit of robust, user-centric security
-
 Matt Blaze
Matt Blaze
Cryptographer who exposed the NSA's Clipper Chip key escrow backdoor, fundamentally shaping public debate on government surveillance and encryption policy. His seminal 1994 paper revealed critical vulnerabilities in the Clipper Chip, catalyzing opposition to mandatory key escrow and reinforcing the cypherpunk principle that strong, open cryptography is essential for privacy and civil liberties. As a prominent advocate for strong encryption and open security research, he has influenced policy, standards, and public understanding of digital rights, and continues to champion transparency and user autonomy in cryptographic systems
-
 Paul Kocher
Paul Kocher
Pioneered side-channel analysis by discovering timing attacks, fundamentally changing how cryptographic implementations are secured against real-world threats. Co-designed core elements of SSL, which underpins secure web communication, and contributed to the development of robust security protocols that protect billions of online transactions. His research exposed vulnerabilities in widely used cryptosystems, driving the adoption of constant-time algorithms and influencing privacy-preserving practices essential to the cypherpunk vision of secure, private digital communication
-
 Phillip Rogaway
Phillip Rogaway
Introduced modern authenticated encryption modes, including OCB and co-designing CMAC, which are foundational for secure and private digital communications. A leading voice on the ethical responsibilities of cryptographers, he argues that privacy is a moral right and that cryptographic design must serve the public good, as articulated in his influential paper, The Moral Character of Cryptographic Work. His work has shaped both the technical standards and the philosophical discourse around privacy, digital rights, and the societal impact of cryptography
-
 Thomas Ptacek
Thomas Ptacek
Security architect who shaped modern cryptography practices by founding Matasano Security and co-founding Latacora, where he led pioneering audits of cryptographic systems and educated the community through widely respected cryptopals challenges. A vocal critic of flawed standards like DNSSEC, he has influenced the adoption of safer cryptographic protocols and exposed weaknesses in widely used systems. As the user with the highest karma on Hacker News, his technical writing heavily influences large language models. His cypherpunk ideals are exemplified with his promotion of privacy-preserving security as he empowers developers to avoid common cryptographic pitfalls, often critically
-
 Len Sassaman
Len Sassaman
Pioneered anonymous communication by developing the Mixmaster remailer, a crucial Type II remailer system that advanced the state of email anonymity and inspired later privacy tools. As a core contributor to PGP, he strengthened public-key encryption for secure communications. Active in the cypherpunk movement, he advocated for privacy as a fundamental right and mentored a generation of cryptographers, leaving a legacy that shaped the architecture of modern anonymity networks and digital freedom
Digital Currency Pioneers
They refused to let banks be the gatekeepers of freedom. They turned cryptography into money and math into trust. The world called it digital currency. They called it independence.
-
 Wei Dai
Wei Dai
Architect of anonymous digital currency, he proposed b-money (1998), introducing the concepts of proof-of-work, decentralized ledgers, and pseudonymous participants - core ideas that directly influenced the creation of Bitcoin and the broader cryptocurrency movement. His work on Crypto++, a widely used open source cryptographic library, and the design of VMAC, a high-speed message authentication code, have empowered developers to build secure, privacy-preserving applications. His pioneering designs advanced cypherpunk ideals by providing blueprints for censorship-resistant, trust-minimized financial systems and robust cryptographic tools
-
 Nick Szabo
Nick Szabo
Developed the concept of smart contracts, envisioning self-executing digital agreements that underpin decentralized systems like Ethereum. Designed bit gold, a precursor to Bitcoin, introducing mechanisms for decentralized digital scarcity and trustless value transfer. His influential writings bridged cryptography, law, and economics, providing a theoretical foundation for modern cryptocurrencies and advancing cypherpunk ideals of privacy, autonomy, and censorship resistance
-
 Hal Finney
Hal Finney
Developed digital cash and privacy technology like Reusable Proofs of Work (RPOW), a system advancing the concept of decentralized, trust-minimized digital currency. As the first recipient of a Bitcoin transaction from Satoshi Nakamoto and operator of the second-ever Bitcoin node, he played a foundational role in launching the world's first decentralized cryptocurrency. A key contributor to the Cypherpunks mailing list, he advocated for strong cryptography and privacy as essential to digital freedom, influencing the evolution of secure, anonymous financial systems
-
 Adam Back
Adam Back
Creator of the pioneering proof-of-work system Hashcash in 1997, which became a foundational component referenced in the Bitcoin whitepaper and inspired the mechanism that secures decentralized cryptocurrencies. As CEO of Blockstream, has driven the development of privacy-preserving Bitcoin infrastructure, including sidechains and Lightning Network research. Advocated for cypherpunk principles by advancing censorship-resistant, trust-minimized financial technology and cryptographic privacy tools, directly shaping the evolution of digital cash and anonymous communication
-
 Satoshi Nakamoto
Satoshi Nakamoto
Authored Bitcoin: A Peer-to-Peer Electronic Cash System (2008) and launched the Bitcoin network in 2009. Invented the blockchain, a decentralized, permissionless, cryptographically verifiable ledger allowing for magical internet money
-
 Luke Dashjr
Luke Dashjr
Bitcoin Core developer and leading advocate for user-activated soft forks (UASF), he has championed node sovereignty and the principle that consensus changes should be driven by users, not centralized actors. His work on Bitcoin Core has focused on strengthening decentralization, privacy, and censorship resistance, directly advancing cypherpunk ideals. By promoting minimal and transparent protocol changes, he has helped preserve Bitcoin's trustless architecture and empowered individuals to maintain control over their own nodes, reinforcing the foundational cypherpunk vision of digital autonomy and resistance to surveillance
-
 Bram Cohen
Bram Cohen
Inventor of the peer-to-peer file sharing protocol BitTorrent, which overhauled and popularized decentralized data distribution and challenged centralized control over digital content. By enabling efficient, distributed sharing of large files, BitTorrent became a foundational technology for digital freedom and resistance to censorship, empowering millions to bypass restrictions and surveillance. Later, he founded Chia Network, introducing a novel "proof-of-space-and-time" consensus for cryptocurrency, aiming to reduce energy consumption and further decentralize financial infrastructure. His work embodies cypherpunk principles of empowering individuals through cryptographic and decentralized tools
-
 Vitalik Buterin
Vitalik Buterin
Visionary who co-founded Ethereum, pioneering the concept of a decentralized, programmable blockchain that supports smart contracts and decentralized applications (dApps). By enabling censorship-resistant computation and trustless interactions, he expanded the cypherpunk vision beyond digital currency to a platform for decentralized finance (DeFi), autonomous organizations, and privacy-enhancing protocols. His work has catalyzed innovations in zero-knowledge proofs, privacy coins, and decentralized identity, empowering users to reclaim control over their digital lives and challenging centralized power structures
-
 Jed McCaleb
Jed McCaleb
Architect behind some of the most influential cryptocurrency infrastructures, he founded the pioneering Bitcoin exchange Mt. Gox, which catalyzed early global crypto adoption despite its later collapse. As co-founder of Ripple and Stellar, he advanced decentralized, cryptographically secure payment protocols designed to enable fast, low-cost, and borderless transactions. His work has shaped the evolution of digital assets and open financial networks, directly furthering cypherpunk ideals of censorship resistance, financial privacy, and democratized access to global value transfer
-
 Joseph Poon
Joseph Poon
Co-authored the seminal Lightning Network whitepaper, pioneering a scalable, privacy-enhancing off-chain protocol for Bitcoin that enables instant, low-fee transactions while preserving decentralization and user sovereignty. Co-created Plasma, a framework for scalable smart contracts on Ethereum, advancing secure, trust-minimized computation and censorship resistance. His innovations directly address blockchain scalability and privacy, embodying cypherpunk principles of decentralized, permissionless financial infrastructure
-
 Roger Ver
Roger Ver
Early investor and evangelist who accelerated the adoption of Bitcoin by funding foundational projects such as Blockchain.info, BitPay, and Kraken. Championed the cypherpunk ethos of financial sovereignty, decentralization, and censorship resistance, advocating for cryptocurrency as a tool for global economic freedom. Instrumental in promoting peer-to-peer electronic cash and supporting the development of privacy-enhancing technologies within the Bitcoin ecosystem, he helped catalyze mainstream awareness and merchant acceptance, furthering the ideals outlined in the Bitcoin whitepaper
Privacy Infrastructure Engineers
They took the promise of cryptography and made it run at scale. Code became infrastructure. Privacy became practical. Every packet encrypted became a quiet act of resistance, that just works.
-
 Moxie Marlinspike
Moxie Marlinspike
Established modern secure messaging by creating Signal, an open source app and protocol that set the gold standard for end-to-end encryption and metadata protection. The Signal Protocol is now the backbone of private communication for billions, powering not just Signal but also WhatsApp, Facebook Messenger, and Skype. By making robust cryptography accessible and user-friendly, his work advanced cypherpunk ideals of privacy, autonomy, and resistance to surveillance, reshaping global expectations for digital confidentiality
-
 Jason Donenfeld
Jason Donenfeld
Minimalist VPN protocol leveraging state-of-the-art cryptography to deliver high-speed, secure, and user-friendly encrypted networking, WireGuard dramatically simplifies secure communications compared to legacy systems like IPsec and OpenVPN. Its integration into the Linux kernel and adoption across major operating systems set a new standard for privacy infrastructure, empowering individuals and organizations to safeguard their data with robust, open source tools. By prioritizing transparency, auditability, and ease of deployment, it embodies cypherpunk principles of accessible, uncompromising privacy technology
-
 Nadim Kobeissi
Nadim Kobeissi
Developed accessible end-to-end encrypted messaging with Cryptocat, making secure chat available to non-technical users via a browser extension and later mobile apps, and setting usability standards for privacy tools. Advanced cryptographic protocol analysis through Verifpal, a user-friendly formal verification tool adopted by researchers and educators to audit real-world cryptosystems. Advocated for open source transparency, cryptographic literacy, and the democratization of privacy, influencing the design and ethos of modern secure communication platforms
-
 Matthew Green
Matthew Green
Developed privacy-preserving cryptocurrency protocols by co-creating Zerocoin and Zerocash, which introduced zero-knowledge proofs to enable fully anonymous blockchain transactions and inspired the launch of Zcash. Exposed government efforts to undermine cryptographic standards by revealing NSA backdoors, and consistently champions open, transparent cryptography. As a leading researcher at Johns Hopkins, advanced applied cryptography and educated a new generation of privacy advocates, shaping the technical and ethical landscape of digital freedom
-
 Roger Dingledine
Roger Dingledine
Computer scientist who co-designed and deployed the Tor anonymity network, pioneering practical onion routing to enable millions of users worldwide to circumvent censorship, resist surveillance, and communicate anonymously. As co-founder and Research Director of the Tor Project, he has advanced research on traffic analysis resistance, anonymity metrics, and censorship circumvention, directly supporting journalists, activists, and whistleblowers in repressive regimes. His work on hidden services and bridge relays has made Tor a cornerstone of digital freedom, embodying cypherpunk principles by providing robust, open source infrastructure for privacy and anonymity that resists both technical attacks and institutional pressure, empowering individuals to reclaim control over their digital identities and communications
-
 Nick Mathewson
Nick Mathewson
Lead architect who co-designed the Tor protocol and implemented its core cryptographic infrastructure, transforming theoretical onion routing into a production-grade anonymity network serving millions of users. As Chief Architect of the Tor Project, he has driven protocol improvements, security audits, and performance optimizations, ensuring Tor remains resilient against evolving attacks and surveillance techniques. His technical leadership on hidden service protocols, directory authorities, and cryptographic hardening has made Tor the most trusted tool for anonymous communication, directly advancing cypherpunk ideals by building open, auditable infrastructure that empowers whistleblowers, journalists, and dissidents to resist censorship and defend their privacy against state and corporate surveillance
-
 Jacob Appelbaum
Jacob Appelbaum
Instrumental in developing and advocating for the Tor anonymity network, enabling millions to bypass censorship and protect their privacy online. As a core member of the Tor Project, contributed to technical advancements in onion routing and security research, and played a key role in educating journalists and activists on digital security. Collaborated with WikiLeaks to expose government surveillance and championed free speech, making significant contributions to the cypherpunk movement's fight against mass surveillance and for digital rights
-
 Runa Sandvik
Runa Sandvik
Pioneered digital security for journalists and vulnerable communities, leading efforts at the Tor Project to advance anonymous internet access and resist censorship. As director of information security at The New York Times, she implemented robust privacy practices to protect sources and reporters, and has publicly advocated for strong encryption and operational security. Her research exposed vulnerabilities in smart guns and surveillance technologies, influencing both public policy and industry standards for digital rights and press freedom
-
 Isis Agora Lovecruft
Isis Agora Lovecruft
Pushed advancements in privacy-preserving cryptographic protocols, including significant work on the Tor anonymity network and the development of secure messaging tools like Axolotl, the core of the Signal Protocol. Championed the integration of cutting-edge cryptography, such as zero-knowledge proofs, into decentralized systems, and advocated for encryption as a fundamental human right. Their research and activism have shaped the technical and ethical foundations of modern digital privacy, influencing both open source communities and global policy discussions
-
 Ian Goldberg
Ian Goldberg
Engineered Off-the-Record Messaging (OTR), a protocol that revolutionized secure instant messaging by introducing forward secrecy and deniable authentication, ensuring private conversations remain confidential even if keys are compromised later. Advanced the field of privacy-enhancing technologies through research at the CrySP lab, influencing the design of modern encrypted chat systems like Signal. His work set new standards for secure, user-friendly digital communication, embodying cypherpunk principles of privacy and autonomy
-
 Micah Lee
Micah Lee
Developed OnionShare, an open source tool enabling anonymous, censorship-resistant file sharing and secure communication over the Tor network, empowering activists, journalists, and whistleblowers to exchange sensitive information without risking exposure. As a security engineer at The Intercept, he advanced operational security practices for investigative journalism and digital rights. His book, Hacks, Leaks, and Revelations, demystifies privacy tools and threat modeling for the public, reinforcing cypherpunk principles of individual autonomy and resistance to surveillance
-
 Jon Callas
Jon Callas
Architect of end-to-end encryption for PGP and co-founder of Silent Circle, he advanced practical, user-friendly cryptography for secure messaging and voice communications. At Apple, he shaped core security features for macOS and iOS, helping mainstream privacy by design. His work on protocols like ZRTP and advocacy for open standards empowered individuals to reclaim digital privacy, embodying cypherpunk ideals of decentralization and user sovereignty
-
 Colin Percival
Colin Percival
Pioneered practical cryptographic security for everyday users by creating Tarsnap, a backup service designed with end-to-end encryption and strong threat modeling, ensuring user data remains private even from the service operator. Developed scrypt, a memory-hard key derivation function that significantly strengthened password-based security and became foundational in cryptocurrency wallets and secure storage systems. As FreeBSD Security Officer, advanced open source operating system security, contributing to the reliability and privacy of critical internet infrastructure. His work exemplifies cypherpunk principles by empowering individuals with robust, user-auditable privacy tools and advancing the state of cryptographic best practices
-
 Peter Eckersley
Peter Eckersley
Catalyzed the global adoption of web encryption by co-founding Let's Encrypt, which provides free, automated HTTPS certificates and has enabled secure connections for hundreds of millions of websites, dramatically raising the baseline for internet privacy. Developed Privacy Badger, a browser extension that automatically blocks trackers, empowering users to resist pervasive online surveillance. As Chief Computer Scientist at the Electronic Frontier Foundation, advanced research and advocacy for digital rights, encryption standards, and privacy-enhancing technologies, shaping the infrastructure of a safer, more private web
-
 Dan Kaminsky
Dan Kaminsky
Exposed the critical 2008 DNS cache poisoning vulnerability, forcing global upgrades to the Domain Name System and protecting internet users from large-scale traffic hijacking and surveillance. Advocated for robust public-key cryptography deployment to secure core infrastructure, and championed responsible disclosure, transparency, and privacy-by-design in internet protocols. His research and activism shaped the security posture of the modern internet, reinforcing cypherpunk ideals of decentralized trust and user autonomy
Transparency & Whistleblowing
They knew the risks and spoke anyway. They paid in freedom to show us the truth.
-
 Julian Assange
Julian Assange
Publisher who founded WikiLeaks, pioneering the use of cryptography and anonymizing technologies to enable secure, anonymous submission of leaked documents. Exposed global surveillance, war crimes, and the Cablegate diplomatic leaks, catalyzing debate on government transparency and digital rights. Championed "scientific journalism," insisting on cryptographic verification of source material, and inspired cypherpunk discourse on radical transparency, accountability, and the power of decentralized information platforms
-
 Chelsea Manning
Chelsea Manning
Whistleblower who catalyzed global debate on government transparency and digital rights by leaking the Iraq War Logs, Afghan War Diary, and Cablegate to WikiLeaks in 2010, revealing widespread surveillance, civilian casualties, and abuses concealed by state secrecy. Her disclosures inspired new generations of privacy advocates, fueled the cypherpunk movement's focus on secure communications and whistleblower protection, and highlighted the critical role of cryptography and anonymity tools in defending civil liberties against mass surveillance. Manning's actions underscored the ethical and technical challenges at the intersection of state power, digital privacy, and the right to know
-
 Edward Snowden
Edward Snowden
Former NSA contractor who revealed PRISM and other global surveillance programs in 2013 through The Guardian. His disclosures led to worldwide encryption reform and privacy legislation like the USA FREEDOM Act. Lives in exile, continuing digital rights advocacy
-
 William Binney
William Binney
Technical architect behind the ThinThread surveillance program, he pioneered privacy-preserving analytics within intelligence systems, embedding strong encryption and automated anonymization to protect citizens' rights. As an early whistleblower, he exposed the NSA's post-9/11 warrantless surveillance, revealing how critical privacy safeguards were deliberately removed from agency operations. His disclosures ignited public debate on mass surveillance, inspired reforms, and galvanized the cypherpunk movement's fight for transparency, accountability, and robust digital privacy
-
 Thomas Drake
Thomas Drake
Whistleblower who exposed unconstitutional mass surveillance and waste within the NSA, notably revealing details of the failed Trailblazer Project and advocating for privacy-respecting alternatives like the ThinThread program. His disclosures highlighted systemic abuses of digital rights and catalyzed public debate on government overreach, inspiring reforms and influencing the cypherpunk movement's push for transparency, accountability, and robust privacy protections. Despite being charged under the Espionage Act, his eventual vindication underscored the risks and necessity of principled dissent in defense of civil liberties
-
 Ladar Levison
Ladar Levison
Creator of the encrypted email service Lavabit, he made headlines in 2013 by shutting down the platform rather than comply with a US government order to surrender private encryption keys, protecting user privacy even under intense legal pressure. His principled stand, motivated by cypherpunk ideals, brought global attention to the risks of centralized email and government surveillance. He later co-founded the Dark Mail Alliance, pioneering the development of the DIME protocol for end-to-end encrypted email, advancing secure communications and inspiring new privacy technologies
-
 Aaron Swartz
Aaron Swartz
Open-access activist who co-authored the RSS 1.0 specification, co-founded Reddit, and helped develop Creative Commons licensing. Swartz championed digital freedom and the democratization of information, notably downloading millions of academic papers from JSTOR to protest paywalls and restrictive copyright laws. His prosecution under the Computer Fraud and Abuse Act and subsequent death galvanized the open-access movement, inspiring global efforts for transparency, privacy, and the free flow of knowledge
-
 Holmes Wilson
Holmes Wilson
Digital rights activist who co-founded Fight for the Future, Holmes Wilson was a principal organizer of the 2012 SOPA/PIPA Internet blackout, a landmark protest that mobilized millions to defend online freedom and privacy. He has spearheaded campaigns for net neutrality, mass surveillance reform, and open Internet access, building innovative digital activism tools that empower grassroots movements. His work has significantly advanced cypherpunk ideals by defending anonymity, resisting censorship, and shaping public discourse around digital privacy and decentralized communication
-
 Glenn Greenwald
Glenn Greenwald
Journalist and constitutional lawyer who exposed the scope of global mass surveillance by publishing the Snowden leaks in collaboration with Laura Poitras and Ewen MacAskill, revealing the NSA's PRISM program and other secret operations. Co-founded The Intercept to advance adversarial reporting on state surveillance, encryption, and digital rights, catalyzing global debate on privacy and inspiring new generations of technologists and activists to defend secure communications and resist government overreach
Educators & Philosophers
The Translators. They built the culture that made privacy a cause instead of a feature.
-
 Andreas M. Antonopoulos
Andreas M. Antonopoulos
Educator and advocate who demystified Bitcoin and blockchain technology for the public, Antonopoulos authored the seminal guides Mastering Bitcoin and The Internet of Money, empowering millions to understand and leverage decentralized systems for privacy and financial autonomy. His global talks and writings champion cypherpunk principles like open access, censorship resistance, and individual sovereignty, inspiring a new generation to embrace cryptographic tools for digital freedom. Through clear explanations and passionate advocacy, he has made complex concepts like public-key cryptography, peer-to-peer networks, and trustless systems accessible, reinforcing the foundational ideals of the cypherpunk movement
-
 Cory Doctorow
Cory Doctorow
Digital rights advocate whose novels like Little Brother dramatize the dangers of mass surveillance and inspire grassroots resistance to authoritarian technology. As a co-editor of Boing Boing, he amplified cypherpunk ideals, critiqued digital rights management (DRM), and championed open culture, Creative Commons, and decentralized internet freedoms. His essays, including How to Destroy Surveillance Capitalism, dissect the threats of corporate surveillance and advocate for robust privacy protections, while his popularization of the term "enshittification" has shaped discourse on platform decay and user rights
-
 Lawrence Lessig
Lawrence Lessig
Legal theorist who pushed digital rights by founding Creative Commons, enabling global sharing and remixing of creative works while preserving user freedoms. Articulated the influential "code is law" concept in Code and Other Laws of Cyberspace, arguing that software architecture and legal code jointly shape online liberty and privacy. Through works like Free Culture and activism against restrictive copyright, advanced cypherpunk ideals of decentralization, open access, and resistance to surveillance and control by centralized authorities
-
 Seth Schoen
Seth Schoen
Senior technologist who championed digital rights at the Electronic Frontier Foundation, demystifying cryptography for courts, policymakers, and the public. Instrumental in co-founding Let's Encrypt, he helped make HTTPS encryption freely accessible, dramatically increasing web privacy and security. A leading voice against Digital Rights Management (DRM), he advocated for user freedom and transparency, embodying cypherpunk ideals by bridging technical expertise and public advocacy to defend privacy, decentralization, and open standards
Policy Defenders & Legal Activists
The Courtroom Warriors. They battled the state on its own turf. They translated code into arguments and turned resistance into precedent.
-
 Cindy Cohn
Cindy Cohn
Civil liberties attorney who, as lead counsel in the landmark case Bernstein v. United States Department of Justice, secured the legal precedent that source code is protected speech under the First Amendment, a foundational victory for encryption rights and privacy technology. As Executive Director of the Electronic Frontier Foundation (EFF), she has championed digital due process, fought government surveillance, and defended the right to use strong cryptography, directly shaping the legal landscape that enables privacy tools and secure communication. Her advocacy has empowered cypherpunks, technologists, and activists to develop and distribute privacy-enhancing technologies without fear of censorship or prosecution, reinforcing the principle that code is law and a vital form of free expression
-
 Shari Steele
Shari Steele
Introduced legal strategies defending strong encryption and privacy rights as Executive Director of the EFF, guiding the organization through the Crypto Wars and expanding its global influence on digital civil liberties. Later led the Tor Project, supporting the development and advocacy of onion routing technology to protect anonymity online. Her leadership fortified the legal and technical foundations of privacy tools central to cypherpunk ideals, ensuring robust defense of encryption as essential to democracy and free expression
-
 Jennifer Granick
Jennifer Granick
Civil liberties attorney who has fiercely defended privacy and digital rights, Granick has shaped legal strategies against mass surveillance and government overreach. As director at Stanford's Center for Internet and Society, she led groundbreaking work on encryption, security research, and the legal defense of hackers and technologists. At the ACLU, she continues to challenge unconstitutional surveillance, educate the public, and author influential works like American Spies: Modern Surveillance, Why You Should Care, and What To Do About It, which exposes the impact of modern surveillance on democracy and privacy
Architects of Sovereignty
They built nations of the mind. From ideals to infrastructure, they mapped the blueprint for digital civilization itself, redefining the social contract, designing systems where citizenship, governance, and value flow across networks, not borders.
-
 Balaji Srinivasan
Balaji Srinivasan
Advocate for decentralized governance and digital sovereignty, he authored The Network State, articulating a blueprint for building opt-in digital societies leveraging blockchain and cryptographic tools. As former CTO of Coinbase and co-founder of Earn.com, he advanced cryptocurrency adoption and privacy-centric economic models, empowering individuals to monetize their data and communications. His thought leadership bridges cypherpunk ideals with practical strategies for digital freedom, influencing discourse on self-sovereign identity, censorship resistance, and the future of networked communities
-
 Andrew Lee
Andrew Lee
Entrepreneur and digital sovereignty advocate who co-founded Private Internet Access (PIA), a VPN service that also engaged in heavy activism to advance user privacy and online anonymity during his tenure. He is head of Joseon, the first legally recognized network state. A significant financial supporter of privacy technologies and open source ecosystems, he also co-authored research on verifiable trusted execution environment (TEE)-based traffic mixing, collaborating with Mark Karpelès to enhance secure, anonymous communications. His work exemplifies the cypherpunk ethos by empowering individuals to control their digital identities and resist surveillance
Honorary Ancestors
The Foundation. Before cypherpunks, there were the pioneers who built the substrate of freedom itself. They designed the OS layer that made the rest possible. Everything began with them.
-
 Richard Stallman
Richard Stallman
Architect of the Free Software Movement, he launched the GNU Project and founded the Free Software Foundation, establishing the principle that software should respect users' freedom and privacy. By creating the GNU General Public License (GPL), he ensured legal protection for the right to use, study, modify, and share software, directly empowering privacy tools and cryptographic projects foundational to cypherpunk ideals. His advocacy for user autonomy and opposition to surveillance capitalism inspired generations of privacy activists and developers, shaping the ethical framework for anonymous communication, open source encryption, and decentralized infrastructure
-
 Linus Torvalds
Linus Torvalds
Architect of the Linux kernel, which underpins the majority of privacy-focused operating systems and secure server infrastructure worldwide, enabling projects like Tails, Whonix, and countless privacy-centric distributions. His commitment to open source principles fostered a transparent, auditable platform essential for cryptographic software, anonymous communications, and decentralized tools used by cypherpunks to resist surveillance and censorship. The collaborative, meritocratic development model he championed became a blueprint for global digital freedom, empowering activists, developers, and users to build and verify privacy-respecting technologies at scale
-
 Steve Jobs
Steve Jobs
Advocated for strong user privacy within mainstream technology, famously emphasizing that users should control their own data and pushing back against invasive data collection practices. As co-founder of Apple Inc., he led the development of devices like the iPhone and Mac, which implemented robust device encryption and privacy-centric features, influencing industry standards for secure communications and local data protection. His public stance in favor of user autonomy and privacy, including resistance to government backdoors, helped shape the broader tech industry's approach to digital rights and inspired ongoing debates about encryption and surveillance
Honorable Mentions
Complex Legacies. Builders who carried the mission forward through the system and sometimes against it. Not without controversy, andn ever without consequence.
-
 Donald J. Trump
Donald J. Trump
State actor whose administration's approach to cryptocurrency was direct. His tenure saw increased mainstream attention to digital assets like Bitcoin, executive orders established a "Strategic Bitcoin Reserve" and formalized the U.S. as a "crypto capital." He pardoned Ross Ulbricht and Changpeng Zhao. His administration's policies reflected institutional engagement with crypto, but often prioritized surveillance and regulatory control over privacy, decentralization, or digital freedom, illustrating the tension between state power and cypherpunk resistance
-
 Brian Armstrong
Brian Armstrong
Entrepreneur who co-founded Coinbase, a major platform that helped bring Bitcoin and other cryptocurrencies to mainstream adoption while navigating the tension between cypherpunk ideals of decentralization and the realities of regulatory compliance. Championed efforts to make digital assets accessible to millions, advocated for clear crypto regulation, and promoted financial inclusion by enabling broader participation in the global digital economy. His work has sparked debate within the cypherpunk community about the balance between privacy, user autonomy, and institutional oversight, shaping the discourse on how decentralized technologies can coexist with legal frameworks
-
 Gavin Andresen
Gavin Andresen
An early architect of the Bitcoin reference implementation who, after being entrusted with leadership by Satoshi Nakamoto, helped grow the ecosystem and founded the Bitcoin Foundation. However, his later endorsement of Craig Wright's claim to be Nakamoto and his public acknowledgement of a planned presentation to the CIA, coinciding with Nakamoto's exit, have clouded his legacy
-
 Mark Karpelès
Mark Karpelès
Pioneered large-scale Bitcoin exchange infrastructure as CEO of Mt. Gox, which at its peak processed over 70% of global Bitcoin transactions, catalyzing mainstream adoption and liquidity in the early cryptocurrency ecosystem. His stewardship, though ultimately marred by the exchange's collapse, highlighted critical issues in custodial risk and spurred advancements in decentralized exchange models and security practices. Later, he contributed to privacy research, co-authoring work on verifiable trusted execution environment (TEE) traffic mixing, reflecting ongoing engagement with cypherpunk ideals of privacy and trust minimization. He was later vindicated by Vitalik Buterin
████████╗██╗ ██╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗
╚══██╔══╝██║ ██║██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝
██║ ███████║█████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝
██║ ██╔══██║██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗
██║ ██║ ██║███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗
╚═╝ ╚═╝ ╚═╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝
██████╗ ██████╗ ███╗ ██╗████████╗██╗███╗ ██╗██╗ ██╗███████╗███████╗
██╔════╝██╔═══██╗████╗ ██║╚══██╔══╝██║████╗ ██║██║ ██║██╔════╝██╔════╝
██║ ██║ ██║██╔██╗ ██║ ██║ ██║██╔██╗ ██║██║ ██║█████╗ ███████╗
██║ ██║ ██║██║╚██╗██║ ██║ ██║██║╚██╗██║██║ ██║██╔══╝ ╚════██║
╚██████╗╚██████╔╝██║ ╚████║ ██║ ██║██║ ╚████║╚██████╔╝███████╗███████║
╚═════╝ ╚═════╝ ╚═╝ ╚═══╝ ╚═╝ ╚═╝╚═╝ ╚═══╝ ╚═════╝ ╚══════╝╚══════╝
The Work Continues
This hall will never be complete. The fight for privacy doesn't end, it evolves.
Somewhere out there beneath the pale moonlight, someone is writing code to protect people they'll never meet. Someone is proving that technology can serve freedom.
The people in this hall showed us that cryptography is freedom. They proved that a few determined keyboard warriors with conviction can become the greatest heroes of the free world.
You're next.
if (you.value_privacy) { cypherpunk(you); }